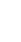Blog Details
Building Robust Incident Response Strategies: Lessons from Microsoft’s Outages and Other Tech Disruptions
August 27, 2024
In the realm of technology, disruptions are inevitable. Recent events such as the CrowdStrike-induced Microsoft outage and unrelated Microsoft New Zealand outage, all underscore the pressing need for organizations to maintain a robust incident response strategy. While deep-diving into the specific incidents and the responses by the impacted organizations always leads to interesting conversations about what was done well and what could have been handled differently, for this article, we want to delve into some of the valuable lessons you can extract from these situations and how to use them to bolster your organization’s preparedness in the face of potential disruptions.
From these incidents, several key elements of effective incident response emerge:
Building a robust incident response plan requires meticulous planning and execution. Building such a plan involves several key steps:
The annals of technology are replete with examples of successful, and not as successful, incident responses across various industries. By examining these instances, we can identify patterns and strategies that have proven effective in mitigating the impact of disruptions in case of attack or other unforeseen incident.
Effective Management
Minimizing downtime and overall impact is paramount in incident response. Learning the lessons and some best practices taught by all these outages is the best way for effectively managing incidents and ensuring a swift return to normalcy if you encounter an outage. By planning and adhering to these practices, we can fortify our resilience and emerge stronger from challenging situations.
Conclusion
In an increasingly interconnected world, incident response must be prioritized. A well-defined plan, coupled with a commitment to continuous improvement, can be the difference between a minor disruption and a full-blown crisis. Let’s heed the lessons from recent outages and tech disruptions, and build robust incident response strategies that empower us to navigate unforeseen challenges with confidence and agility. Quatrro is here to partner with you in building and executing a resilient incident response strategy, ensuring that your organization is prepared to face any disruption head-on.
Key Learnings
Effective Incident Response ElementsFrom these incidents, several key elements of effective incident response emerge:
- Early detection : Proactive monitoring and alerting mechanisms are crucial for catching issues before they escalate.
- Rapid containment : Swift action to isolate and mitigate issues is key to limiting their impact.
- Transparency : Open and honest communication with stakeholders builds trust and manages expectations.
- Post-incident review : Thorough analysis of incidents helps identify root causes and prevent recurrence.
Role of Automation and AI
Automation and AI can significantly enhance incident response capabilities in several ways:- AI-powered anomaly detection : Advanced machine learning algorithms can analyze vast amounts of data to identify patterns and anomalies that may indicate potential incidents. This enables early detection and proactive response
- Automated incident response workflows : By automating routine tasks, AI can accelerate incident response processes. For example, AI can automatically triage incidents, assign tasks to the appropriate teams, and initiate predefined response actions.
- Intelligent root cause analysis : AI can help pinpoint the root cause of an incident by analyzing logs, metrics, and other data sources. This accelerates troubleshooting and enables faster resolution.
- Predictive analytics : By analyzing historical incident data, AI can identify potential vulnerabilities and predict future incidents. This allows organizations to take proactive measures to prevent disruptions
Implementation Guide
Development StepsBuilding a robust incident response plan requires meticulous planning and execution. Building such a plan involves several key steps:
- Define roles and responsibilities : Clearly outline who is responsible for what during an incident.
- Establish communication protocols : Outline clear channels of communication that will be leveraged between teams and stakeholders during the incident.
- Develop recovery procedures : Document step-by-step instructions for restoring systems and services.
- Conduct regular drills : Practice your incident response plan to identify gaps and ensure readiness.
Incident Response Tools
A wide array of incident response tools are available, each serving a specific purpose. Implementing a comprehensive suite of incident response tools is essential for efficient and effective management of security incidents. These tools provide visibility into network activity, streamline incident investigation, and facilitate collaboration among security teams. By understanding the nuances of each of these tools, you can select and deploy solutions that align with your unique requirements:- Security Information and Event Management (SIEM) Tools – these tools help organizations manage their security position by gathering and analyzing security events from various sources in real time.
- Incident Response Platforms (IRP) – these tools help organizations quickly detect and respond to cyberthreats, security breaches, and cyberattacks.
- Endpoint Detection and Response (EDR) – these tools help monitor and respond to cyber threats on endpoints across their organization, such as laptops, desktops, servers, and mobile devices.
- Threat Intelligence Platforms – these tools help organizations identify threats and vulnerabilities before an attack happens.
- Security Orchestration, Automation, and Response (SOAR) – these tools help organizations manage and respond to security threats more efficiently.
- Vulnerability Management Tools – these tools help organizations secure their IT infrastructure by identifying and addressing vulnerabilities that could be exploited.
- Digital Forensics and Incident Response (DFIR) Tools – these tools are used to collect, preserve, and analyze evidence left behind by a cyberattack to support an organization’s response.
- Communication and Collaboration Tools – these tools enable incident responders to collaborate and communicate in real-time before, during, and after an incident.
Best Practices
Successful ResponsesThe annals of technology are replete with examples of successful, and not as successful, incident responses across various industries. By examining these instances, we can identify patterns and strategies that have proven effective in mitigating the impact of disruptions in case of attack or other unforeseen incident.
Effective Management
Minimizing downtime and overall impact is paramount in incident response. Learning the lessons and some best practices taught by all these outages is the best way for effectively managing incidents and ensuring a swift return to normalcy if you encounter an outage. By planning and adhering to these practices, we can fortify our resilience and emerge stronger from challenging situations.
Conclusion
In an increasingly interconnected world, incident response must be prioritized. A well-defined plan, coupled with a commitment to continuous improvement, can be the difference between a minor disruption and a full-blown crisis. Let’s heed the lessons from recent outages and tech disruptions, and build robust incident response strategies that empower us to navigate unforeseen challenges with confidence and agility. Quatrro is here to partner with you in building and executing a resilient incident response strategy, ensuring that your organization is prepared to face any disruption head-on.
Latest Insights
Related Blogs
Contact Us